Identifying a Threat Actor Profile
Commercial threat intelligence providers and well-resourced government agencies often attribute malicious activity to a particular threat actor or actor group.
Scenario
In this scenario, a threat actor group named “Disco Team” is modeled using STIX Threat Actor and Identity objects. Disco Team operates primarily in Spanish and they have been known to steal credit card information for financial gain. They use the e-mail alias “disco-team@stealthemail.com” publicly and are known alternatively as “Equipo del Discoteca”.
Data model
Threat actor identification is, as you would expect, represented using the Threat Actor STIX Domain Object (SDO). Information relevant to threat actors, such as goals and motivations, can be captured within this object. Other basic information not specific to threat actors, such as contact information, is best represented using an Identity SDO. Identity objects can also be used for more than threat actors in STIX. They can model organizations, government agencies, and information sources to name a few.
It is important to note that the Disco Team group operates as a Threat Actor and not an Intrusion Set in this scenario. They could potentially support an intrusion set, but that information is unknown. An Intrusion Set is best used to describe an entire attack set that would include multiple campaigns and purposes. In this instance, Disco Team is a self-named threat actor operating with one purpose in mind.
The name and threat_actor_types properties are the only required properties needed for a Threat Actor SDO. The threat_actor_types field is important for describing what type of threat actor Disco Team is. Because Disco Team is regarded as large, organized, and driven to steal financial information, they are best represented with the threat actor type crime-syndicate.
The Threat Actor SDO can also model optional properties that construct a more complete threat actor profile. The aliases field, for instance, contains a list of other names this threat actor is known to be called. A threat actor may also have one or more roles that describe more about what they do. For instance, a threat actor could sponsor or direct attacks, author malware, or operate malicious infrastructure. In the case of Disco Team, they operate as an agent, carrying out attacks that steal financial information on behalf of themselves.
Like most threat actors, Disco Team has a specific goal in mind for their attacks. Therefore, a list of goals describes what the threat actor is trying to do. In this case, Disco Team’s only goal is stealing credit card credentials. Threat actors also have varying degrees of expertise, so the sophistication level of the attacker, if known, can describe the attacker’s skill and knowledge. Disco Team is labeled as expert due to advanced attack methods and proficiency with tools or malicious code. Their resource_level of organization indicates that they are large and well-funded, more so than smaller individuals or teams. Finally, threat actors usually have one or several motivations behind their attacks. The primary_motivation field describes the main reason for attacking. Some threat actors may seek notoriety or dominance, while others are strictly doing it for revenge or personal satisfaction. For Disco Team, obtaining financial information falls under the motivation of personal-gain.
Basic identifying information of the threat actor can be modeled with the Identity SDO. For Disco Team, they are a type of organization, which the identity_class field captures. This is due to this threat actor being more formal and organized, rather than an individual hacker or informal group of hackers. Another property that captures contact_information, if known for the identity, represents any email addresses or phone numbers. For Disco Team, an email address is provided.
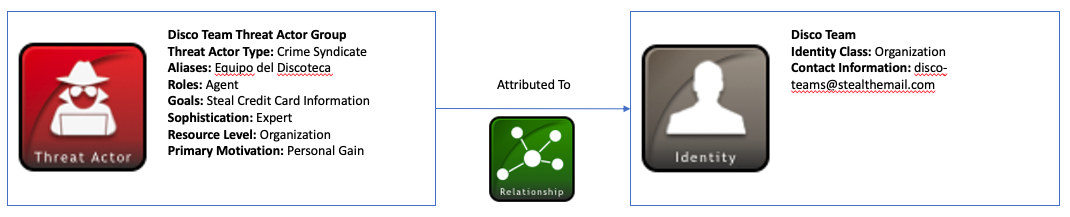
Now that the information for Disco Team is represented in the Threat Actor and Identity SDO’s, the Relationship SRO links the two objects together. In this example, the source_ref threat actor id is attributed-to the target_ref identity id:
A diagram of this relationship below shows the Threat Actor and Identity SDO’s and the Relationship SRO (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and vocabularies, check out the links below:
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
{
"type": "bundle",
"id": "bundle--601cee35-6b16-4e68-a3e7-9ec7d755b4c3",
"objects": [
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--dfaa8d77-07e2-4e28-b2c8-92e9f7b04428",
"created": "2014-11-19T23:39:03.893Z",
"modified": "2014-11-19T23:39:03.893Z",
"name": "Disco Team Threat Actor Group",
"description": "This organized threat actor group operates to create profit from all types of crime.",
"threat_actor_types": [
"crime-syndicate"
],
"aliases": [
"Equipo del Discoteca"
],
"roles": [
"agent"
],
"goals": [
"Steal Credit Card Information"
],
"sophistication": "expert",
"resource_level": "organization",
"primary_motivation": "personal-gain"
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--733c5838-34d9-4fbf-949c-62aba761184c",
"created": "2016-08-23T18:05:49.307Z",
"modified": "2016-08-23T18:05:49.307Z",
"name": "Disco Team",
"description": "Disco Team is the name of an organized threat actor crime-syndicate.",
"identity_class": "organization",
"contact_information": "disco-team@stealthemail.com"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a2e3efb5-351d-4d46-97a0-6897ee7c77a0",
"created": "2020-02-29T18:01:28.577Z",
"modified": "2020-02-29T18:01:28.577Z",
"relationship_type": "attributed-to",
"source_ref": "threat-actor--dfaa8d77-07e2-4e28-b2c8-92e9f7b04428",
"target_ref": "identity--733c5838-34d9-4fbf-949c-62aba761184c"
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
from stix2.v21 import (ThreatActor, Identity, Relationship, Bundle)
threat_actor = ThreatActor(
id="threat-actor--dfaa8d77-07e2-4e28-b2c8-92e9f7b04428",
created="2014-11-19T23:39:03.893Z",
modified="2014-11-19T23:39:03.893Z",
name="Disco Team Threat Actor Group",
description="This organized threat actor group operates to create profit from all types of crime.",
threat_actor_types=["crime-syndicate"],
aliases=["Equipo del Discoteca"],
roles=["agent"],
goals=["Steal Credit Card Information"],
sophistication="expert",
resource_level="organization",
primary_motivation="personal-gain"
)
identity = Identity(
id="identity--733c5838-34d9-4fbf-949c-62aba761184c",
created="2016-08-23T18:05:49.307Z",
modified="2016-08-23T18:05:49.307Z",
name="Disco Team",
description="Disco Team is the name of an organized threat actor crime-syndicate.",
identity_class="organization",
contact_information="disco-team@stealthemail.com"
)
relationship = Relationship(threat_actor, 'attributed-to', identity)
bundle = Bundle(objects=[threat_actor, identity, relationship])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == threat_actor:
print("------------------")
print("== THREAT ACTOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Threat Actor Types: " + str(obj.threat_actor_types))
print("Aliases: " + str(obj.aliases))
print("Roles: " + str(obj.roles))
print("Goals: " + str(obj.goals))
print("Sophistication: " + obj.sophistication)
print("Resource Level: " + obj.resource_level)
print("Primary Motivation: " + obj.primary_motivation)
elif obj == identity:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Identity Class: " + obj.identity_class)
print("Contact Information: " + obj.contact_information)
elif obj == relationship:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)