Introduction to STIX
What is STIX?
Structured Threat Information Expression (STIX) is a language and serialization format used to exchange cyber threat intelligence (CTI). STIX is open source and free allowing those interested to contribute and ask questions freely.
Why should you care?
Contributing and ingesting CTI becomes a lot easier. With STIX, all aspects of suspicion, compromise and attribution can be represented clearly with objects and descriptive relationships. STIX information can be visually represented for an analyst or stored as JSON to be quickly machine readible. STIX's openness allows for integration into existing tools and products or utilized for your specific analyst or network needs.
What's New in STIX 2.1
STIX 2.1 differs from STIX 2.0 in the following ways:
- New objects: Grouping, Infrastructure, Language-Content (internationalization), Location, Malware-Analysis, Note, Opinion
- Objects that have undergone significant change: Malware, all SCOs
- New concepts: Confidence
- STIX Cyber-observable Objects can now be directly related using STIX Relationship Objects
- Renamed conflicting properties on Directory Object, File Object, Process Object, and Windows Registry Key Object.
- Added relationship from Indicator to Observed Data called “based-on”.
- Added a description to Sighting and added a name to Location.
- Made some SCO relationships external on Domain-Name, IPv4-Addr, and IPv6-Addr.
STIX 2.1 Objects
STIX Objects categorize each piece of information with specific attributes to be populated. Chaining multiple objects together through relationships allow for easy or complex representations of CTI. Below is a list of what can be represented through STIX. More detail and visual representations can be found here.
STIX 2.1 defines 18 STIX Domain Objects (SDOs):
| Object | Name | Description |
|---|---|---|
| Attack Pattern | A type of TTP that describe ways that adversaries attempt to compromise targets. | |
| Campaign | A grouping of adversarial behaviors that describes a set of malicious activities or attacks (sometimes called waves) that occur over a period of time against a specific set of targets. | |
| Course of Action | A recommendation from a producer of intelligence to a consumer on the actions that they might take in response to that intelligence. | |
| Grouping | Explicitly asserts that the referenced STIX Objects have a shared context, unlike a STIX Bundle (which explicitly conveys no context). | |
| Identity | Actual individuals, organizations, or groups (e.g., ACME, Inc.) as well as classes of individuals, organizations, systems or groups (e.g., the finance sector). | |
| Indicator | Contains a pattern that can be used to detect suspicious or malicious cyber activity. | |
| Infrastructure | Represents a type of TTP and describes any systems, software services and any associated physical or virtual resources intended to support some purpose (e.g., C2 servers used as part of an attack, device or server that are part of defence, database servers targeted by an attack, etc.). | |
| Intrusion Set | A grouped set of adversarial behaviors and resources with common properties that is believed to be orchestrated by a single organization. | |
| Location | Represents a geographic location. | |
| Malware | A type of TTP that represents malicious code. | |
| Malware Analysis | The metadata and results of a particular static or dynamic analysis performed on a malware instance or family. | |
| Note | Conveys informative text to provide further context and/or to provide additional analysis not contained in the STIX Objects, Marking Definition objects, or Language Content objects which the Note relates to. | |
| Observed Data | Conveys information about cyber security related entities such as files, systems, and networks using the STIX Cyber-observable Objects (SCOs). | |
| Opinion | An assessment of the correctness of the information in a STIX Object produced by a different entity. | |
| Report | Collections of threat intelligence focused on one or more topics, such as a description of a threat actor, malware, or attack technique, including context and related details. | |
| Threat Actor | Actual individuals, groups, or organizations believed to be operating with malicious intent. | |
| Tool | Legitimate software that can be used by threat actors to perform attacks. | |
| Vulnerability | A mistake in software that can be directly used by a hacker to gain access to a system or network. |
STIX 2 defines two STIX Relationship Objects (SROs):
| Object | Name | Description |
|---|---|---|
| Relationship | Used to link together two SDOs or SCOs in order to describe how they are related to each other. | |
| Sighting | Denotes the belief that something in CTI (e.g., an indicator, malware, tool, threat actor, etc.) was seen. |
A look at the structure
STIX 2 objects are represented in JSON. The following is a JSON-based example of a STIX 2.1 Campaign object:
{
"type": "campaign",
"id": "campaign--8e2e2d2b-17d4-4cbf-938f-98ee46b3cd3f",
"spec_version": "2.1",
"created": "2016-04-06T20:03:00.000Z",
"modified": "2016-04-06T20:03:23.000Z",
"name": "Green Group Attacks Against Finance",
"description": "Campaign by Green Group against targets in the financial services sector."
}
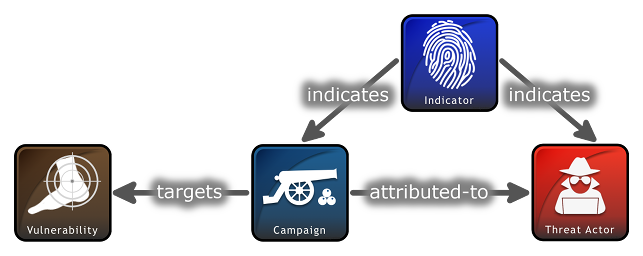 STIX 2 Relationship Example
STIX 2 Relationship Example
Complete information for STIX 2 is available on the OASIS Cyber Threat Intelligence (CTI) Technical Committee (TC) website. Specification documents, schemas and tools are also available.