Indicator for Malicious URL
A very common method for delivering malware to potential targets is to host it at a particular URL. Targets are then directed to that URL via a phishing e-mail or a link from another site and, when they reach it, are exploited. Sharing lists of malicious URLs can be an effective and cheap way to limit exposure to malicious code.
Scenario
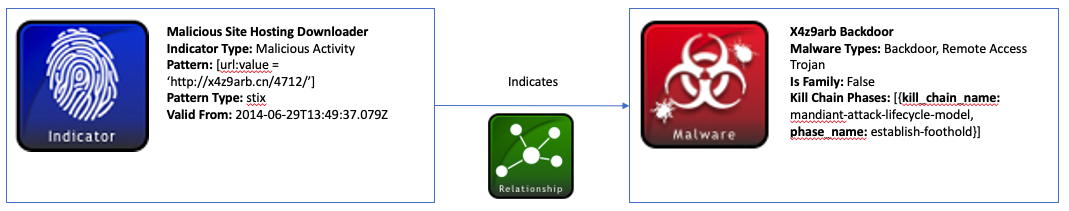
This scenario consists of an indicator for the URL http://x4z9arb.cn/4712/, which is known to be malicious, and a backdoor piece of malware associated with the URL. The site has been shown to host this backdoor malware, and the malware has been known to download remote files.
Data model
Malicious URL values are just one of many indicators that can be represented using the Indicator STIX Domain Object (SDO). This is accomplished using the Indicator SDO’s pattern property which is based on the STIX patterning language. Using this language, the URL can be structured using a comparison expression: [url:value= 'http://x4z9arb.cn/4712/'].
This Indicator object must also contain a indicator_types property that provides more context about the URL. The URL in this scenario is known to be malicious so the appropriate type for this Indicator is malicious-activity. This value is taken from an Indicator Type open vocabulary which contains other useful types for categorizing indicators.
Another required field for Indicator objects called valid_from dictates the time from which this URL should be considered worthwhile intelligence. In this case, the URL is valid from the time the object was created.
The malware associated with the URL in this scenario is a type of backdoor and can be modeled using the STIX Malware SDO. Like with the Indicator object, Malware objects can be further classified using a malware_types property that comes from the Malware Types open vocabulary. For instance, a piece of malware might be classified as a keylogger, spyware, worm, virus, etc. In this example, the malware affiliated with the URL is a type of backdoor and remote-access-trojan.
A Malware SDO can also be useful for capturing kill chain information about the malware instance. It is known that this piece of malware attempts to establish a backdoor foothold and download remote files. Therefore, the Malware object represents this with a kill_chain_phases list which contains both the name of the kill chain used and the phase within that kill chain. For this scenario, the Mandiant Attack Lifecycle Model was used as the kill chain and contains the phase_name establish-foothold. Other kill chains such as Lockheed Martin’s or organization-specific ones can be used as well.
Finally, a Relationship SRO can be used to link the Indicator and Malware objects. The URL Indicator indicates the backdoor Malware object. In this relationship, the indicator id is the source_ref, and the malware id is the target_ref.
A diagram of this relationship below shows the Indicator and Malware SDO’s and the Relationship SRO between them (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and STIX patterning, check out the links below:
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
{
"type": "bundle",
"id": "bundle--56be2a3b-1534-4bef-8fe9-602926274089",
"objects": [
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f",
"created": "2014-06-29T13:49:37.079Z",
"modified": "2014-06-29T13:49:37.079Z",
"name": "Malicious site hosting downloader",
"description": "This organized threat actor group operates to create profit from all types of crime.",
"indicator_types": [
"malicious-activity"
],
"pattern": "[url:value = 'http://x4z9arb.cn/4712/']",
"pattern_type": "stix",
"valid_from": "2014-06-29T13:49:37.079Z"
},
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--162d917e-766f-4611-b5d6-652791454fca",
"created": "2014-06-30T09:15:17.182Z",
"modified": "2014-06-30T09:15:17.182Z",
"name": "x4z9arb backdoor",
"description": "This malware attempts to download remote files after establishing a foothold as a backdoor.",
"malware_types": [
"backdoor",
"remote-access-trojan"
],
"is_family": false,
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "establish-foothold"
}
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--864af2ea-46f9-4d23-b3a2-1c2adf81c265",
"created": "2020-02-29T18:03:58.029Z",
"modified": "2020-02-29T18:03:58.029Z",
"relationship_type": "indicates",
"source_ref": "indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f",
"target_ref": "malware--162d917e-766f-4611-b5d6-652791454fca"
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
from stix2.v21 import (Indicator, KillChainPhase, Malware, Relationship, Bundle)
indicator = Indicator(
id="indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f",
created="2014-06-29T13:49:37.079Z",
modified="2014-06-29T13:49:37.079Z",
name="Malicious site hosting downloader",
description="This organized threat actor group operates to create profit from all types of crime.",
indicator_types=["malicious-activity"],
pattern="[url:value = 'http://x4z9arb.cn/4712/']",
pattern_type="stix",
valid_from="2014-06-29T13:49:37.079000Z"
)
foothold = KillChainPhase(
kill_chain_name="mandiant-attack-lifecycle-model",
phase_name="establish-foothold"
)
malware = Malware(
id="malware--162d917e-766f-4611-b5d6-652791454fca",
created="2014-06-30T09:15:17.182Z",
modified="2014-06-30T09:15:17.182Z",
name="x4z9arb backdoor",
malware_types=["backdoor", "remote-access-trojan"],
description="This malware attempts to download remote files after establishing a foothold as a backdoor.",
kill_chain_phases=[foothold],
is_family="false"
)
relationship = Relationship(indicator, 'indicates', malware)
bundle = Bundle(objects=[indicator, malware, relationship])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == malware:
print("------------------")
print("== MALWARE ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Malware Types: " + str(obj.malware_types))
print("Is Family:" + str(obj.is_family))
print("Kill Chain: " + str(obj.kill_chain_phases))
elif obj == indicator:
print("------------------")
print("== INDICATOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Indicator Types: " + str(obj.indicator_types))
print("Pattern: " + obj.pattern)
print("Pattern Type: " + obj.pattern_type)
print("Valid From: " + str(obj.valid_from))
elif obj == relationship:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)