Malware Indicator for File Hash
A commonly-shared form of threat intelligence as practiced today is the sharing of host-based indicators for malicious code, which are most often file names and hashes. This example describes a file hash indicator and the name and type of the piece of malware that it indicates.
Scenario
This scenario consists of the description of a simple indicator that represents a pattern for a file with a given hash and the context that if a file with that hash is seen it might indicate a sample of Poison Ivy is present.
Data model
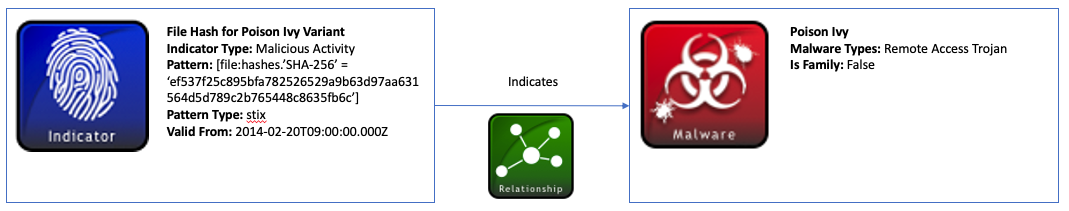
An Indicator STIX Domain Object (SDO) is used to model patterns of expression such as the Poison Ivy file hash in this example. This hash is represented using the pattern property of the Indicator object which is based on the STIX patterning language. With this language, a comparison expression of the SHA-256 hash looks like: [file:hashes.'SHA-256'= 'ef537f25c895bfa782526529a9b63d97aa631564d5d789c2b765448c8635fb6c']. If known, other file attributes such as names or paths can be represented. Also, while this example covers just a file hash, many other Cyber Observable Objects and their properties can be modeled using Indicator patterns. For instance, email messages, domains, IP addresses, and processes are just a few examples.
Indicator objects also require a indicator_types property which helps to define what type of indicator is being represented. In this scenario, the hash value is associated with Poison Ivy, a known nefarious type of malware, so this indicator is labeled as malicious-activity. This value is taken from the Indicator Type open vocabulary which provides other useful types for classifying indicators.
Next, the details of the Poison Ivy malware are captured using a STIX Malware object. Malware objects in STIX also contain a required malware_types property that is needed to specify the type of malware. In this case, Poison Ivy is a remote-access-trojan. This value comes from the Malware Type open vocabulary, which contains several common types of malware categories such as virus, backdoor, spyware, etc.
These SDO’s are then coupled together via a Relationship STIX Relationship Object (SRO). This Relationship connects the source_ref, Indicator, with the target_ref, Malware, via an indicates relationship_type.
A diagram of this relationship below shows the Indicator and Malware SDO’s and the Relationship SRO between them (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and STIX patterning, check out the links below:
- Common Properties
- Vocabularies
- Malware
- Indicator
- Relationship
- STIX Patterning
- Cyber Observable Objects
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
{
"type": "bundle",
"id": "bundle--2a25c3c8-5d88-4ae9-862a-cc3396442317",
"objects": [
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--a932fcc6-e032-476c-826f-cb970a5a1ade",
"created": "2014-02-20T09:16:08.989Z",
"modified": "2014-02-20T09:16:08.989Z",
"name": "File hash for Poison Ivy variant",
"description": "This file hash indicates that a sample of Poison Ivy is present.",
"indicator_types": [
"malicious-activity"
],
"pattern": "[file:hashes.'SHA-256' = 'ef537f25c895bfa782526529a9b63d97aa631564d5d789c2b765448c8635fb6c']",
"pattern_type": "stix",
"valid_from": "2014-02-20T09:00:00Z"
},
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--fdd60b30-b67c-41e3-b0b9-f01faf20d111",
"created": "2014-02-20T09:16:08.989Z",
"modified": "2014-02-20T09:16:08.989Z",
"name": "Poison Ivy",
"malware_types": [
"remote-access-trojan"
],
"is_family": false
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--29dcdf68-1b0c-4e16-94ed-bcc7a9572f69",
"created": "2020-02-29T18:09:12.808Z",
"modified": "2020-02-29T18:09:12.808Z",
"relationship_type": "indicates",
"source_ref": "indicator--a932fcc6-e032-476c-826f-cb970a5a1ade",
"target_ref": "malware--fdd60b30-b67c-41e3-b0b9-f01faf20d111"
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
from stix2.v21 import (Indicator, Malware, Relationship, Bundle)
indicator = Indicator(
id="indicator--a932fcc6-e032-476c-826f-cb970a5a1ade",
created="2014-02-20T09:16:08.989Z",
modified="2014-02-20T09:16:08.989Z",
name="File hash for Poison Ivy variant",
description="This file hash indicates that a sample of Poison Ivy is present.",
indicator_types=["malicious-activity"],
pattern="[file:hashes.'SHA-256' = 'ef537f25c895bfa782526529a9b63d97aa631564d5d789c2b765448c8635fb6c']",
pattern_type="stix",
valid_from="2014-02-20T09:00:00.000000Z"
)
malware = Malware(
id="malware--fdd60b30-b67c-41e3-b0b9-f01faf20d111",
created="2014-02-20T09:16:08.989Z",
modified="2014-02-20T09:16:08.989Z",
name="Poison Ivy",
malware_types=["remote-access-trojan"],
is_family="false"
)
relationship = Relationship(indicator, 'indicates', malware)
bundle = Bundle(objects=[indicator, malware, relationship])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == malware:
print("------------------")
print("== MALWARE ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Type: " + obj.type)
print("Malware Types: " + str(obj.malware_types))
print("Is Family:" + str(obj.is_family))
elif obj == indicator:
print("------------------")
print("== INDICATOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Indicator Types: " + str(obj.indicator_types))
print("Pattern: " + obj.pattern)
print("Pattern Type: " + obj.pattern_type)
print("Valid From: " + str(obj.valid_from))
elif obj == relationship:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)