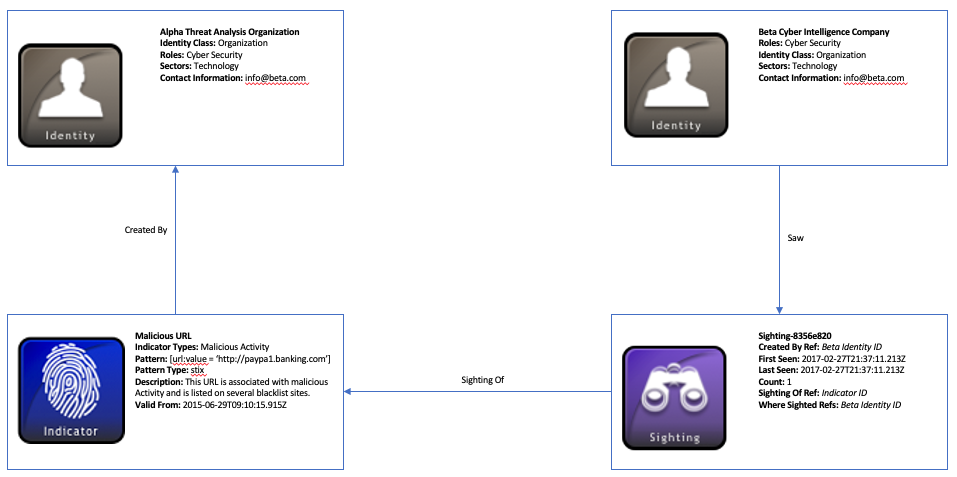
Sighting of an Indicator
A major benefit of cyber threat intelligence sharing and collaboration is the ability to alert other companies and agencies ahead of time that an indicator is present on a system or network. This allows for a more proactive approach in addressing cyber threats. In many cases, an indicator that was spotted on one network is also seen on another network. Being able to share that a particular indicator was seen elsewhere is vital to other organizations consuming this information.
Scenario
This scenario consists of two cyber threat companies, Alpha and Beta, who share threat intelligence. A malicious URL was seen on Alpha’s network and an indicator was generated to capture this information. Alpha then shares this information with company Beta who later sees this indicator on their systems. Beta then creates a sighting of this indicator to share that this indicator has been spotted.
Data model
In this example, there are two Identity STIX Domain Objects (SDOs) used for the two companies: Alpha and Beta. The Identity objects document relevant information about the two organizations, such as what sector they are in, what they do, and contact information. Both organizations are producers and consumers of STIX intelligence, so their id’s can be referenced within objects using the created_by_ref property to indicate they are the originators of the STIX objects they generate. It is worth noting that Identity SDO’s can also be used to represent individuals, attack targets, government agencies, and groups, to name a few.
Identity objects at the very minimum need a couple of required properties: name and identity_class. The identity_class field is important for categorizing the type of identity Alpha and Beta represent. In both their cases, this field would be populated with the value organization. This term comes from the identity class open vocabulary, which contains suggested values for labeling identities.
The other fields within the Identity SDO are optional but help to structure a complete profile of the identity. For instance, it might be useful to know the list of roles an individual or group may perform, which is captured with the roles property. Since both companies in this scenario deal with cyber threats, it makes sense to have them labeled as cyber security. If you know the list of sectors the identities may belong to or any relevant contact_information, this can be provided as well for these objects. For example, knowing that some STIX object creators are in the financial sector may provide more context as to why they are seeing certain indicators or being targeted by specific threat actors. Both of the companies in this example operate in the technology sector, which comes from the industry sector open vocabulary.
Next, the Alpha company uses an Indicator SDO to capture information about the malicious URL they discovered on their network. Using the STIX patterning language, Alpha represents the URL as a comparison expression in the pattern property: [url:value = 'http://paypa1.banking.com']. Since Alpha knows this URL is nefarious, they label this Indicator as malicious-activity using the indicator_types field which comes from the Indicator Type open vocabulary.
The Beta company receives this indicator intelligence from Alpha and implements it on their own network to look for this specific URL. Once they spot it, they generate a Sighting STIX Relationship Object (SRO), which is a special type of relationship object that differs from the regular Relationship SRO. For instance, Sighting contains unique properties like count, first_seen, and last_seen that convey when a SDO was seen within a particular timeframe as well as the number of times this SDO was seen. Alternatively, a standard Relationship SRO is simply used to connect two SDO’s together and does not provide the same type of intelligence assertions.
In this example, Beta’s Sighting object captures information about Alpha’s Indicator which they spotted on their network. Since they are the creator of this object as well as the victim in this instance, Beta’s Identity ID is represented in the created_by_ref and where_sighted_refs properties respectively. It is worth mentioning that the where_sighted_refs field is a list, so it can also list other Identity SDO ID’s where this indicator was seen. Another reference, sighting_of_ref, contains the ID of the SDO that was sighted, which in this case is the Indicator object. This is a required property due to the fact you cannot have a Sighting without an object to sight.
In some cases, an indicator like a URL can be spotted several times on a network over a significant period of time. For this scenario, however, Beta only spotted the URL once which results in the count field reflecting an integer value of “1”. Since it was just seen once, the first_seen, and last_seen properties portray the same timestamp.
A diagram of this scenario below shows the Identity and Indicator SDO’s and the Sighting SRO (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and vocabularies, check out the links below:
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
{
"type": "bundle",
"id": "bundle--2ac7882f-76a3-4a9b-97b3-811b3af1c7c0",
"objects": [
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--9299f726-ce06-492e-8472-2b52ccb53191",
"created_by_ref": "identity--39012926-a052-44c4-ae48-caaf4a10ee6e",
"created": "2017-02-27T13:57:10.515Z",
"modified": "2017-02-27T13:57:10.515Z",
"name": "Malicious URL",
"description": "This URL is potentially associated with malicious activity and is listed on several blacklist sites.",
"indicator_types": [
"malicious-activity"
],
"pattern": "[url:value = 'http://paypa1.banking.com']",
"pattern_type": "stix",
"valid_from": "2015-06-29T09:10:15.915Z"
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--39012926-a052-44c4-ae48-caaf4a10ee6e",
"created": "2017-02-24T15:50:10.564Z",
"modified": "2017-02-24T15:50:10.564Z",
"name": "Alpha Threat Analysis Org.",
"roles": [
"Cyber Security"
],
"identity_class": "organization",
"sectors": [
"technology"
],
"contact_information": "info@alpha.org"
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--5206ba14-478f-4b0b-9a48-395f690c20a2",
"created": "2017-02-26T17:55:10.442Z",
"modified": "2017-02-26T17:55:10.442Z",
"name": "Beta Cyber Intelligence Company",
"roles": [
"Cyber Security"
],
"identity_class": "organization",
"sectors": [
"technology"
],
"contact_information": "info@beta.com"
},
{
"type": "sighting",
"spec_version": "2.1",
"id": "sighting--8356e820-8080-4692-aa91-ecbe94006833",
"created_by_ref": "identity--5206ba14-478f-4b0b-9a48-395f690c20a2",
"created": "2017-02-28T19:37:11.213Z",
"modified": "2017-02-28T19:37:11.213Z",
"first_seen": "2017-02-27T21:37:11.213Z",
"last_seen": "2017-02-27T21:37:11.214Z",
"count": 1,
"sighting_of_ref": "indicator--9299f726-ce06-492e-8472-2b52ccb53191",
"where_sighted_refs": [
"identity--5206ba14-478f-4b0b-9a48-395f690c20a2"
]
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
from stix2.v21 import (Identity, Indicator, Sighting, Bundle)
identityAlpha = Identity(
id="identity--39012926-a052-44c4-ae48-caaf4a10ee6e",
created="2017-02-24T15:50:10.564Z",
modified="2017-02-24T15:50:10.564Z",
name="Alpha Threat Analysis Org.",
identity_class="organization",
contact_information="info@alpha.org",
roles=["Cyber Security"],
sectors=["technology"],
spec_version="2.1",
type="identity"
)
identityBeta = Identity(
id="identity--5206ba14-478f-4b0b-9a48-395f690c20a2",
created="2017-02-26T17:55:10.442Z",
modified="2017-02-26T17:55:10.442Z",
name="Beta Cyber Intelligence Company",
identity_class="organization",
contact_information="info@beta.com",
roles=["Cyber Security"],
sectors=["technology"],
spec_version="2.1",
type="identity"
)
indicator = Indicator(
id="indicator--9299f726-ce06-492e-8472-2b52ccb53191",
created_by_ref="identity--39012926-a052-44c4-ae48-caaf4a10ee6e",
created="2017-02-27T13:57:10.515Z",
modified="2017-02-27T13:57:10.515Z",
name="Malicious URL",
description="This URL is potentially associated with malicious activity and is listed on several blacklist sites.",
indicator_types=["malicious-activity"],
pattern="[url:value = 'http://paypa1.banking.com']",
pattern_type="stix",
valid_from="2015-06-29T09:10:15.915Z",
spec_version="2.1",
type="indicator"
)
sighting = Sighting(
id="sighting--8356e820-8080-4692-aa91-ecbe94006833",
created_by_ref="identity--5206ba14-478f-4b0b-9a48-395f690c20a2",
created="2017-02-28T19:37:11.213Z",
modified="2017-02-28T19:37:11.213Z",
first_seen="2017-02-27T21:37:11.213Z",
last_seen="2017-02-27T21:37:11.214Z",
count=1,
sighting_of_ref="indicator--9299f726-ce06-492e-8472-2b52ccb53191",
where_sighted_refs=["identity--5206ba14-478f-4b0b-9a48-395f690c20a2"],
spec_version="2.1",
type="sighting"
)
bundle = Bundle(objects=[indicator, identityAlpha, identityBeta, sighting])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == identityAlpha:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Roles: " + str(obj.roles))
print("Identity Class: " + obj.identity_class)
print("Sectors: " + str(obj.sectors))
print("Contact Information: " + obj.contact_information)
elif obj == identityBeta:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Roles: " + str(obj.roles))
print("Identity Class: " + obj.identity_class)
print("Sectors: " + str(obj.sectors))
print("Contact Information: " + obj.contact_information)
elif obj == indicator:
print("------------------")
print("== INDICATOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Indicator Types: " + str(obj.indicator_types))
print("Pattern: " + obj.pattern)
print("Pattern Type: " + obj.pattern_type)
print("Valid From: " + str(obj.valid_from))
elif obj == sighting:
print("------------------")
print("== SIGHTING ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Created by Ref: " + obj.created_by_ref)
print("First Seen: " + str(obj.first_seen))
print("Last Seen: " + str(obj.last_seen))
print("Count: " + str(obj.count))
print("Sighting of Ref: " + obj.sighting_of_ref)
print("Where Sighted Refs: " + str(obj.where_sighted_refs))