Threat Actor Leveraging Attack Patterns and Malware
A large part of the reason for doing threat actor attribution and correlation is to develop an understanding of the adversary behavior in order to better prioritize courses of action and defend against those types of attacks. In many cases, adversary behavior can be characterized by the types of attack patterns they typically use: for example, using spear phishing as a delivery mechanism for malware is an attack pattern. In other cases, behavior can be described based on the malware that the adversary typically uses.
Scenario
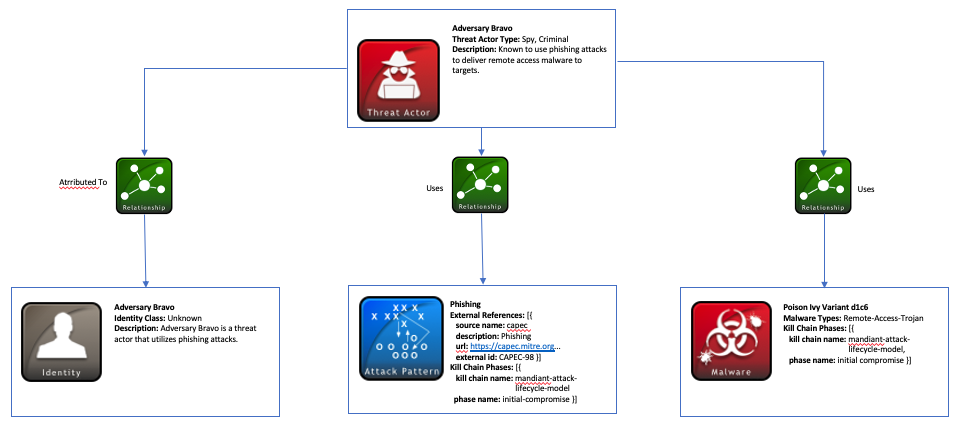
This scenario represents a threat actor known as “Adversary Bravo”. Adversary Bravo is known to use phishing attacks to deliver remote access malware to the targets. The malware variety they typically use is a variant on the Poison Ivy malware.
Data model
Any known characteristics and attributes of Adversary Bravo can be modeled using the Threat Actor STIX Domain Object (SDO). This object captures information specific to the threat actor, such as other aliases, motivations for attacking, and roles they may have in an attack. Sometimes this information is not fully known, which is the case for Adversary Bravo. Therefore, you only need to specify required properties for the Threat Actor object which consist of a name and a list of threat_actor_types. The threat_actor_types field categorizes the type of threat actor based on the threat-actor-type vocabulary. In this instance we can infer that by using Poison Ivy malware to establish a remote backdoor, Adversary Bravo may be performing nefarious activity or spying which results in types of criminal and spy.
Other basic identifying information about Adversary Bravo is captured with an Identity SDO. In this scenario, this object is used for a threat actor identity, but it can also represent organizations, governments, and other entities. It is useful for capturing sectors this Identity may be affiliated with as well as relevant contact information. In the case of Adversary Bravo, there is little information about this identity, so the required identity_class property, based on the identity class vocabulary, would be unknown. The Identity SDO can be linked with the Threat Actor SDO by using a Relationship object. The type of relationship between the 2 objects, represented by the relationship_type field, would contain a value of attributed-to, meaning this threat actor is attributed to this identity.
The malware in this scenario is a Poison Ivy variant d1c6 which can be represented using a Malware SDO. It is required for every Malware object to incorporate a list of malware types to describe the malware. Since this is a type of remote trojan, the malware_types property would contain the value remote-access-trojan which comes from the malware type vocabulary. You can label malware objects with more than one value however, as some may likely have more than one capability. For instance, a particular type of malware could be both a keylogger and spyware. Another relationship can be established between this Malware SDO and the Threat Actor SDO. In this case, the relationship_type between the two objects would be uses. The Threat Actor uses the Malware.
Adversary Bravo uses phishing as a delivery mechanism for the Poison Ivy malware which can be represented using an Attack Pattern SDO. In addition to providing more context about what the threat actor is trying to do, Attack Pattern objects are useful for representing taxonomies such as CAPEC with the external_references field. Common Attack Pattern Enumeration and Classification (CAPEC™) is a dictionary of potential attack patterns, so in this case by looking in that dictionary the producer could see that “CAPEC-98” is the ID for phishing and can label the external_id as such. A Relationship SRO once again links the Threat Actor to this Attack Pattern object with a relationship_type of uses.
One other useful concept that is seen in both the Malware and Attack Pattern objects is the ability to capture kill chain information. For instance, certain attack patterns, malware, and tools might be used to establish a foothold or move laterally once a system has been compromised. In this example, the Poison Ivy malware and phishing attack pattern are associated with the kill chain phase initial-compromise, since the threat actor is attempting to establish an initial backdoor with the Poison Ivy variant. This phase is from the Mandiant Attack Lifecycle Model, but you are not limited to using any specific type of kill chain.
A diagram below shows the objects used in this scenario (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and vocabularies, check out the links below:
- Common Properties
- Vocabularies
- Threat Actor
- Identity
- Attack Pattern
- Malware
- Relationship
- Kill Chain Phase
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
{
"type": "bundle",
"id": "bundle--0ecd8123-90d5-46e0-9cd4-65d4999b3a2e",
"objects": [
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"created": "2015-05-07T14:22:14.760Z",
"modified": "2015-05-07T14:22:14.760Z",
"name": "Adversary Bravo",
"description": "Adversary Bravo is known to use phishing attacks to deliver remote access malware to the targets.",
"threat_actor_types": [
"spy",
"criminal"
]
},
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--d1c612bc-146f-4b65-b7b0-9a54a14150a4",
"created": "2015-04-23T11:12:34.760Z",
"modified": "2015-04-23T11:12:34.760Z",
"name": "Poison Ivy Variant d1c6",
"malware_types": [
"remote-access-trojan"
],
"is_family": false,
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "initial-compromise"
}
]
},
{
"type": "attack-pattern",
"spec_version": "2.1",
"id": "attack-pattern--8ac90ff3-ecf8-4835-95b8-6aea6a623df5",
"created": "2015-05-07T14:22:14.760Z",
"modified": "2015-05-07T14:22:14.760Z",
"name": "Phishing",
"description": "Spear phishing used as a delivery mechanism for malware.",
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "initial-compromise"
}
],
"external_references": [
{
"source_name": "capec",
"description": "phishing",
"url": "https://capec.mitre.org/data/definitions/98.html",
"external_id": "CAPEC-98"
}
]
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--1621d4d4-b67d-41e3-9670-f01faf20d111",
"created": "2015-05-10T16:27:17.760Z",
"modified": "2015-05-10T16:27:17.760Z",
"name": "Adversary Bravo",
"description": "Adversary Bravo is a threat actor that utilizes phishing attacks.",
"identity_class": "unknown"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d44019b6-b8f7-4cb3-837e-7fd3c5724b87",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "uses",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "malware--d1c612bc-146f-4b65-b7b0-9a54a14150a4"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3cd2d6f9-0ded-486b-8dca-606283a8997f",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "uses",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "attack-pattern--8ac90ff3-ecf8-4835-95b8-6aea6a623df5"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--56e5f1c8-08f3-4e24-9e8e-f87d844672ec",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "attributed-to",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "identity--1621d4d4-b67d-41e3-9670-f01faf20d111"
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
from stix2.v21 import (ThreatActor, Identity, AttackPattern, Campaign, IntrusionSet, Relationship, ExternalReference, Bundle)
threat_actor = ThreatActor(
id="threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
created="2015-05-07T14:22:14.760Z",
modified="2015-05-07T14:22:14.760Z",
name="Adversary Bravo",
description="Adversary Bravo is known to use phishing attacks to deliver remote access malware to the targets.",
threat_actor_types=["spy", "criminal"],
spec_version="2.1",
type="threat-actor"
)
identity = Identity(
id="identity--1621d4d4-b67d-41e3-9670-f01faf20d111",
created="2015-05-10T16:27:17.760Z",
modified="2015-05-10T16:27:17.760Z",
name="Adversary Bravo",
description="Adversary Bravo is a threat actor that utilizes phishing attacks.",
identity_class="unknown",
spec_version="2.1",
type="identity"
)
init_comp = KillChainPhase(
kill_chain_name="mandiant-attack-lifecycle-model",
phase_name="initial-compromise"
)
malware = Malware(
id="malware--d1c612bc-146f-4b65-b7b0-9a54a14150a4",
created="2015-04-23T11:12:34.760Z",
modified="2015-04-23T11:12:34.760Z",
name="Poison Ivy Variant d1c6",
malware_types=["remote-access-trojan"],
kill_chain_phases=[init_comp],
spec_version="2.1",
type="malware",
is_family="false"
)
ref = ExternalReference(
source_name="capec",
description="phishing",
url="https://capec.mitre.org/data/definitions/98.html",
external_id="CAPEC-98"
)
attack_pattern = AttackPattern(
id="attack-pattern--8ac90ff3-ecf8-4835-95b8-6aea6a623df5",
created="2015-05-07T14:22:14.760Z",
modified="2015-05-07T14:22:14.760Z",
name="Phishing",
description="Spear phishing used as a delivery mechanism for malware.",
kill_chain_phases=[init_comp],
external_references=[ref],
spec_version="2.1",
type="attack-pattern"
)
relationship1 = Relationship(threat_actor, 'uses', malware)
relationship2 = Relationship(threat_actor, 'uses', attack_pattern)
relationship3 = Relationship(threat_actor, 'attributed-to', identity)
bundle = Bundle(objects=[threat_actor, malware, attack_pattern, identity, relationship1, relationship2, relationship3])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == threat_actor:
print("------------------")
print("== THREAT ACTOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Threat Actor Types: " + str(obj.threat_actor_types))
elif obj == identity:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Identity Class: " + obj.identity_class)
elif obj == malware:
print("------------------")
print("== MALWARE ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Type: " + obj.type)
print("Malware Types: " + str(obj.malware_types))
print("Is Family:" + str(obj.is_family))
print("Kill Chain: " + str(obj.kill_chain_phases))
elif obj == attack_pattern:
print("------------------")
print("== ATTACK PATTERN ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Kill Chain Phases: " + str(obj.kill_chain_phases))
print("External References: " + str(obj.external_references))
elif obj == relationship1:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)
elif obj == relationship2:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)
elif obj == relationship3:
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)