Using Granular Markings
Having finer, more granular restrictions over what cyber threat intelligence is shared is beneficial for organizations who are hesitant to sharing certain information. This element of control allows STIX producers to limit the accessibility of specific data to organizations with which they share intelligence.
Scenario
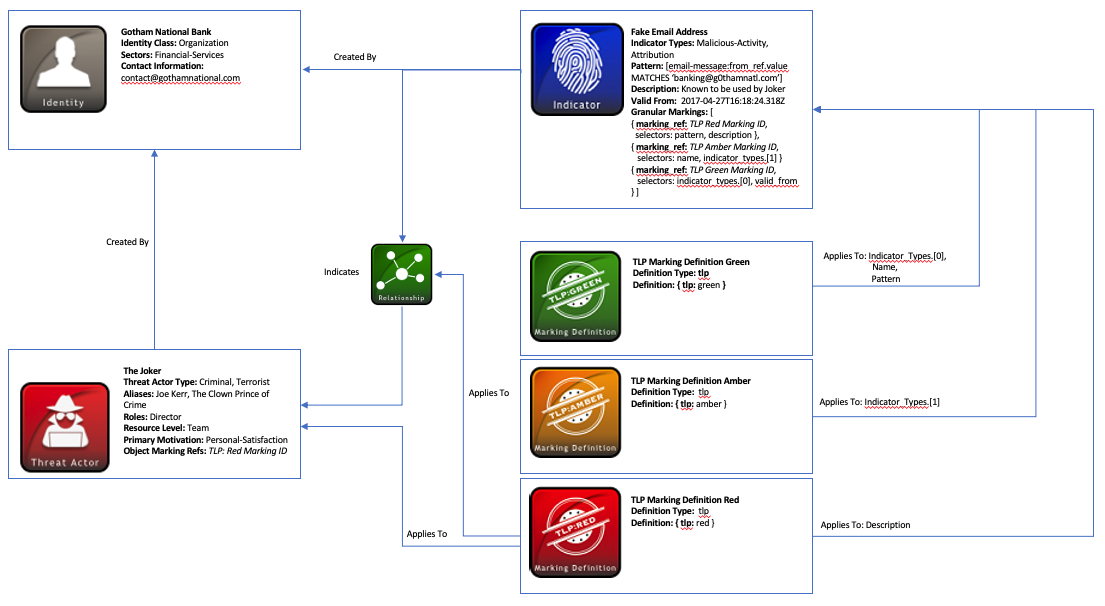
This scenario focuses on a STIX producer, “Gotham National Bank”, who imposes granular markings on an Indicator object. Before sharing this indicator, Gotham selects a few “Traffic Light Protocol” (TLP) marking definitions to apply to the indicator. These marking definitions help restrict the usage of certain properties of the indicator based on its TLP marking type.
Data model
The producer of STIX objects in this scenario, Gotham National Bank, can be represented with an Identity STIX Domain Object (SDO). Like with all STIX objects, an id attribute uniquely identifies Gotham National and can be referenced within all the objects they generate with the created_by_ref property. Although created_by_ref is optional, this is helpful for attributing the Indicator SDO directly to Gotham and allows any consumers to see who applied the TLP markings to the Indicator. The Identity object is also useful for listing other relevant details about Gotham such as contact_information and what type of identity they are with the identity_class field.
In order to enforce limitations on specific properties of the Indicator object, Gotham decided to use TLP Marking Definition objects. This particular marking definition type, which can be seen within the STIX 2.1 specification under TLP Marking Object Type, helps specify the type of restriction they want to impose. For instance, in this scenario, they needed to utilize three defined TLP marking definitions, each with a different restriction type. With all of these objects, the definition_type is required and must be tlp. In addition, the definition property is also required and must contain one of the four types of TLP. Gotham needed three of the four types of TLP definitions, which were green, amber, and red. To read about each of the four types of TLP and what restrictions they specify, check out US-CERT’s TLP Definitions and Usage. Knowing these types is useful for the level of restriction you would like to provide for both objects and properties of objects.
A point of emphasis worth noting is that the TLP Marking Object Types defined in the STIX 2.1 specification must be used to represent TLP markings. Gotham or any other producer could not create their own TLP markings but could create organization-specific Statement Marking Object Types. Both of these types, TLP and Statement, also cannot be versioned like other STIX objects, which is why there is no modified property on either of these types. To understand more about versioning objects, check out this helpful tutorial video on How to Use Versioning in STIX 2.
Now that Gotham has selected the appropriate TLP Marking Object types, they can be applied to other STIX objects or properties of objects. In the first part of this scenario, they are attached to properties of an Indicator SDO Gotham generated. This Indicator was created to represent a fake email address suspected in emailing the bank's members asking for their credentials. Due to the sensitivity of some of the information contained within this Indicator, they applied different TLP markings to individual portions of this object with the granular_markings property. This property is a list that contains Marking Definition object ID references with the marking_ref field, and a selectors property that specifies the content that should be marked with this marking definition. For instance, Gotham felt the need to apply a strict TLP: Red marking to the description field since this gives certain sensitive intelligence about the threat actor in this scenario (discussed later). To illustrate further, within the granular_markings field of the Indicator, the marking_ref property would contain the marking definition ID for TLP: Red and the selectors list would hold the value description.
For other Indicator properties, Gotham used less restrictive TLP markings than TLP: Red. One required Indicator property is a list of labels, which gives more context about the type of indicator being modeled. In this property list, Gotham labeled this indicator as both malicious-activity and attribution. Both types in the list come from the STIX 2.1 specification's Indicator Type vocabulary. Gotham decided to apply the less restrictive TLP: Green marking to malicious-activity and felt a the more restrictive TLP: Amber marking was needed for attribution. In order to communicate two different markings like this on the indicator_types property, the first label in the list is represented as indicator_types[0], and the second as indicator_types[1]. To illustrate this, the JSON sample below shows how these would be marked if we were just marking the indicator_types field only (Note: Marking Definition ID starting with “f88…” is TLP: Amber and the ID starting with “340…” is TLP: Green):
{
"granular_markings": [
{
"marking_ref": "marking-definition--f88d31f6-486f-44da-b317-01333bde0b82",
"selectors": [
"indicator_types.[1]"
]
},
{
"marking_ref": "marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da",
"selectors": [
"indicator_types.[0]",
]
}
]}
Along with these Indicator indicator_types, Gotham chose to mark the properties name and pattern as TLP: Green. They can mark any property they would like but cannot mark invalid properties such as indicator_types[3], or kill_chain_phases[0] since these are not present currently within this Indicator SDO.
Gotham also created a Threat Actor SDO to capture information about the threat actor this Indicator indicates. In this example, the threat actor, whose name is known as The Joker, has been attributed to the fake email indicator. Along with name, this object helps to structure other information about The Joker such as aliases, roles, and a primary_motivation. Since all of this intelligence is considered sensitive to Gotham National, they marked the entire object as TLP: Red using object markings instead of granular markings. This is accomplished through a property inherent in all SDO's and STIX Relationship Object's (SRO's) called object_marking_refs, which lists all the marking definition IDs that apply to this object. Unlike the granular_markings property that would apply to different fields within Threat Actor, the object_marking_refs applies to the entire Threat Actor SDO.
The final piece of intelligence in this scenario is a Relationship SRO that connects the Indicator and Threat Actor SDO's together. In this relationship, a relationship_type property specifies that this Indicator indicates the Threat Actor. Due to the fact this Relationship object links to a TLP: Red marked object, Gotham also marked it as TLP: Red once again using the object_marking_refs field within Relationship.
The full JSON representation can be seen at the very end of this example and a diagram of the scenario is illustrated below (An interactive version can be found here):
Further Reading
To read more about the objects in this example as well as common properties and vocabularies, check out the links below:
- Common Properties
- Vocabularies
- Identity
- Indicator
- Threat Actor
- Relationship
- Marking Definitions
- Granular Markings
- Object Markings
- Statement Marking Object Type
- TLP Object Marking Type
- STIX Patterning
- Using Versioning in STIX 2
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
{
"type": "bundle",
"id": "bundle--f0af3c36-a642-4cb0-8526-b4ca899cc1db",
"objects": [
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
"created": "2017-04-27T16:18:24.318Z",
"modified": "2017-04-27T16:18:24.318Z",
"name": "Gotham National Bank",
"identity_class": "organization",
"sectors": [
"financial-services"
],
"contact_information": "contact@gothamnational.com"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--1ed8caa7-a708-4706-b651-f1186ede6ca1",
"created_by_ref": "identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
"created": "2017-04-27T16:18:24.318Z",
"modified": "2017-04-27T16:18:24.318Z",
"name": "Fake email address",
"description": "Known to be used by The Joker.",
"indicator_types": [
"malicious-activity",
"attribution"
],
"pattern": "[email-message:from_ref.value MATCHES '.+\\\\banking@g0thamnatl\\\\.com$']",
"pattern_type": "stix",
"valid_from": "2017-04-27T16:18:24.318Z",
"granular_markings": [
{
"marking_ref": "marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed",
"selectors": [
"description"
]
},
{
"marking_ref": "marking-definition--f88d31f6-486f-44da-b317-01333bde0b82",
"selectors": [
"indicator_types.[1]"
]
},
{
"marking_ref": "marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da",
"selectors": [
"indicator_types.[0]",
"name",
"pattern"
]
}
]
},
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--8b6297fe-cae7-47c6-9256-5584b417849c",
"created_by_ref": "identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
"created": "2017-04-27T16:18:24.318Z",
"modified": "2017-04-27T16:18:24.318Z",
"name": "The Joker",
"threat_actor_types": [
"terrorist",
"criminal"
],
"aliases": [
"Joe Kerr",
"The Clown Prince of Crime"
],
"roles": [
"director"
],
"resource_level": "team",
"primary_motivation": "personal-satisfaction",
"object_marking_refs": [
"marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3d1dd3cc-eb47-4704-9c77-ceff2971b95c",
"created": "2017-04-27T16:18:24.318Z",
"modified": "2017-04-27T16:18:24.318Z",
"relationship_type": "indicates",
"source_ref": "indicator--1ed8caa7-a708-4706-b651-f1186ede6ca1",
"target_ref": "threat-actor--8b6297fe-cae7-47c6-9256-5584b417849c",
"object_marking_refs": [
"marking-definition--5e57c739-391a-4eb3-b6be-7d15ca92d5ed"
]
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
from stix2.v21 import (GranularMarking, ThreatActor, Identity, Indicator, Relationship, Bundle, TLP_RED, TLP_AMBER, TLP_GREEN)
granular_red = GranularMarking(
marking_ref=TLP_RED.id,
selectors=["description"]
)
granular_amber = GranularMarking(
marking_ref=TLP_AMBER.id,
selectors=["indicator_types.[1]"]
)
granular_green = GranularMarking(
marking_ref=TLP_GREEN.id,
selectors=["indicator_types.[0]", "name", "pattern"]
)
identity = Identity(
id="identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
created="2017-04-27T16:18:24.318Z",
modified="2017-04-27T16:18:24.318Z",
name="Gotham National Bank",
contact_information="contact@gothamnational.com",
identity_class="organization",
sectors=["financial-services"],
spec_version="2.1",
type="identity"
)
threat_actor = ThreatActor(
id="threat-actor--8b6297fe-cae7-47c6-9256-5584b417849c",
created="2017-04-27T16:18:24.318Z",
modified="2017-04-27T16:18:24.318Z",
created_by_ref="identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
name="The Joker",
threat_actor_types=["terrorist", "criminal"],
aliases=["Joe Kerr", "The Clown Prince of Crime"],
roles=["director"],
resource_level="team",
primary_motivation="personal-satisfaction",
object_marking_refs=[TLP_RED],
spec_version="2.1",
type="threat-actor"
)
indicator = Indicator(
id="indicator--1ed8caa7-a708-4706-b651-f1186ede6ca1",
created="2017-04-27T16:18:24.318Z",
modified="2017-04-27T16:18:24.318Z",
created_by_ref="identity--b38dfe21-7477-40d1-aa90-5c8671ce51ca",
name="Fake email address",
description="Known to be used by The Joker.",
indicator_types=["malicious-activity", "attribution"],
pattern="[email-message:from_ref.value MATCHES '.+\\\\banking@g0thamnatl\\\\.com$']",
pattern_type="stix",
valid_from="2017-04-27T16:18:24.318Z",
granular_markings=[granular_red, granular_amber, granular_green],
spec_version="2.1",
type="indicator"
)
rel = Relationship(
id="relationship--3d1dd3cc-eb47-4704-9c77-ceff2971b95c",
created="2017-04-27T16:18:24.318Z",
modified="2017-04-27T16:18:24.318Z",
relationship_type='indicates',
source_ref="indicator--1ed8caa7-a708-4706-b651-f1186ede6ca1",
target_ref="threat-actor--8b6297fe-cae7-47c6-9256-5584b417849c",
object_marking_refs=[TLP_RED],
spec_version="2.1",
type="relationship"
)
bundle = Bundle(objects=[identity, indicator, threat_actor, rel])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
from stix2.v21 import (Bundle)
for obj in bundle.objects:
if obj == identity:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Identity Class: " + obj.identity_class)
print("Sectors: " + str(obj.sectors))
print("Contact Information: " + obj.contact_information)
elif obj == indicator:
print("------------------")
print("== INDICATOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Type: " + obj.type)
print("Indicator Types: " + str(obj.indicator_types))
print("Pattern: " + obj.pattern)
print("Pattern Type: " + obj.pattern_type)
print("Valid From: " + str(obj.valid_from))
elif obj == marking_def_amber:
print("------------------")
print("== MARKING DEFINITION ==")
print("------------------")
print("ID: " + obj.id)
print("Type: " + obj.type)
print("Created: " + str(obj.created))
print("Definition Type: " + obj.definition_type)
print("Definition: " + str(obj.definition))
elif obj == marking_def_statement:
print("------------------")
print("== MARKING DEFINITION ==")
print("------------------")
print("ID: " + obj.id)
print("Type: " + obj.type)
#print("Name: " + obj.name)
print("Created: " + str(obj.created))
print("Definition Type: " + obj.definition_type)
print("Definition: " + str(obj.definition))