Defining Campaigns vs. Threat Actors vs. Intrusion Sets
Cyber attacks are often leveraged by threat actors as part of a coordinated campaign against a specific target. These campaigns typically have a goal or objective in mind. Sometimes, these campaigns are orchestrated by threat actors from a nation state, crime syndicate or other nefarious organization and contain similar properties, behaviors and attributes in order to achieve many objectives over a significant period of time. This entire attack package is known as an intrusion set.
Scenario
This scenario represents an advanced persistent threat (APT) intrusion set that is suspected to be funded by the country “Franistan”. Their target is the Branistan People’s Party (BPP), one of the political parties of the country “Branistan”. This intrusion set consists of a couple of sophisticated campaigns and attack patterns against the BPP’s website. One campaign seeks to insert false information into the BPP’s web pages, while another is a DDoS effort against the BPP web servers.
Data model
To start with, information about Franistan and the Branistan People’s Party is modeled using Identity STIX Domain Objects (SDO’s). As mentioned in other STIX examples (for instance, see Identifying a Threat Actor Profile), this object is used specifically for representing common identifiable information about Franistan and BPP. The Identity objects in this scenario are best used to help establish relationships among other objects using the STIX Relationship Object (SRO). For example, Franistan is attributed to a threat actor and the BPP is a target of an intrusion set and multiple campaigns.
Next, the details of the advanced persistent threat in this example are represented within the Intrusion Set SDO. This Intrusion Set object, which is labeled with the name APT BPP, contains any motivations as well as goals the intrusion set is trying to achieve. Some of the objectives for APT BPP, listed in the goals property, are to Influence the Branistan election and Disrupt the BPP. Therefore, their motivations are similar, with their primary_motivation being ideology, and one of their secondary_motivations being dominance. Also, since they are suspected to be highly funded and resourced by Franistan, their resource_level would be government. The values for motivations and resource level come from the open vocabularies Attack Motivation and Attack Resource level respectively.
Like with many intrusion sets, there can be multiple threat actors (see Threat Actor SDO) and campaigns that play a part. In this scenario, there is one threat actor simply called Fake BPP whose goal is to also influence the election in Branistan. The motivations and resource_level are also the same as the Intrusion Set SDO, which makes sense since this Threat Actor has been associated with this APT. Fake BPP is suspected to be funded by Franistan, which means the threat_actor_types property that characterizes this threat actor would be nation-state. Other pertinent information can be found in the roles and sophistication properties. In this case, Fake BPP is the orchestrator of these attacks against Branistan, so the roles field would label them as a director. Since they are known to be well-funded and advanced state actors associated with APT-level attacks, Fake BPP’s sophistication level would be considered strategic. The values for roles and sophistication can be found in the open vocabularies of the 2.1 specification under Threat Actor Role and Threat Actor Sophistication respectively.
A couple of different campaigns have been linked to this threat actor and are a part of this intrusion set. These details are appropriately captured within two Campaign SDOs. The first campaign, called Operation Bran Flakes, was orchestrated by Fake BPP in order to hack the Branistan People’s Party’s website www.bpp.bn and inject fake information into it’s web pages. The second reported attack campaign, titled Operation Raisin Bran, occurred later and attempted to flood the BPP web servers to deny legitimate users from accessing the site.
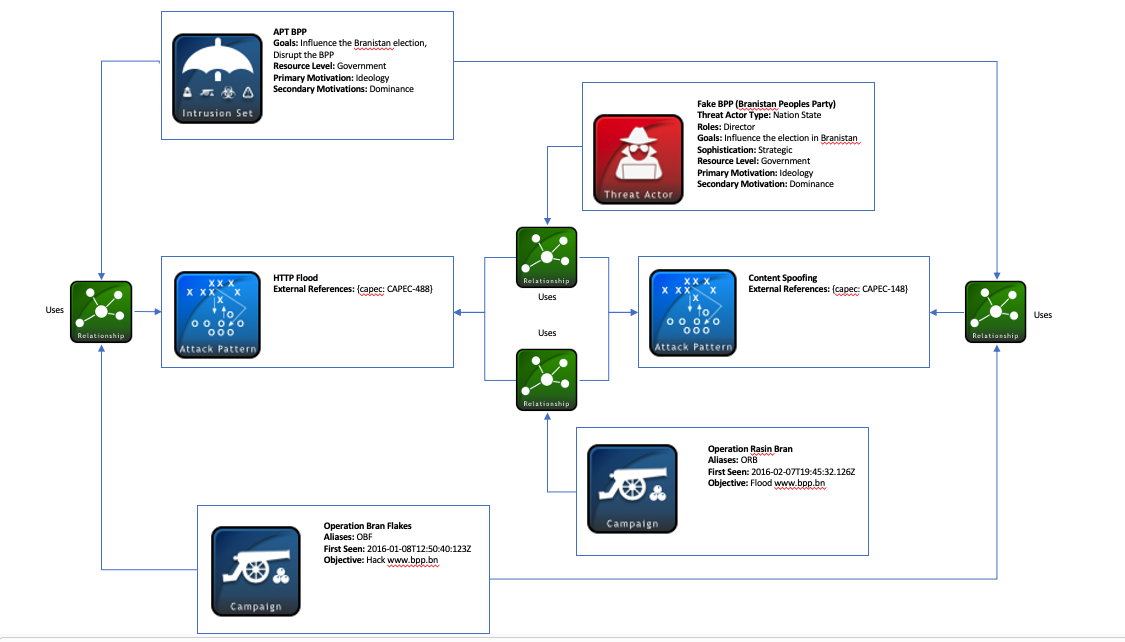
In addition to the attack details modeled in the Campaign objects, Attack Pattern SDO’s help classify these specific attacks using Common Attack Pattern Enumeration and Classification (CAPEC). Within these type of objects, you can find references to the CAPEC ID’s under the external_references property. For instance, the first campaign which attempted to insert false information would fall under external_id CAPEC-148, or “Content Spoofing”. The second Attack Pattern SDO which is associated with the denial of service campaign, references external_id CAPEC-488, or “HTTP Flood”.
Now that we have covered all the STIX Domain Objects in this example, we can examine the relationships, or STIX Relationship Objects (SROs), among them. The attack patterns are used by the threat actor, intrusion set, and campaigns in this scenario, so there are multiple SROs created to represent these relationships. In all of these relationships, the source_ref would reference either the threat actor, intrusion set, or campaign ID’s, and the target_ref would point to either of the attack pattern ID’s mentioned in this example. The relationship_type property would simply be labeled uses.
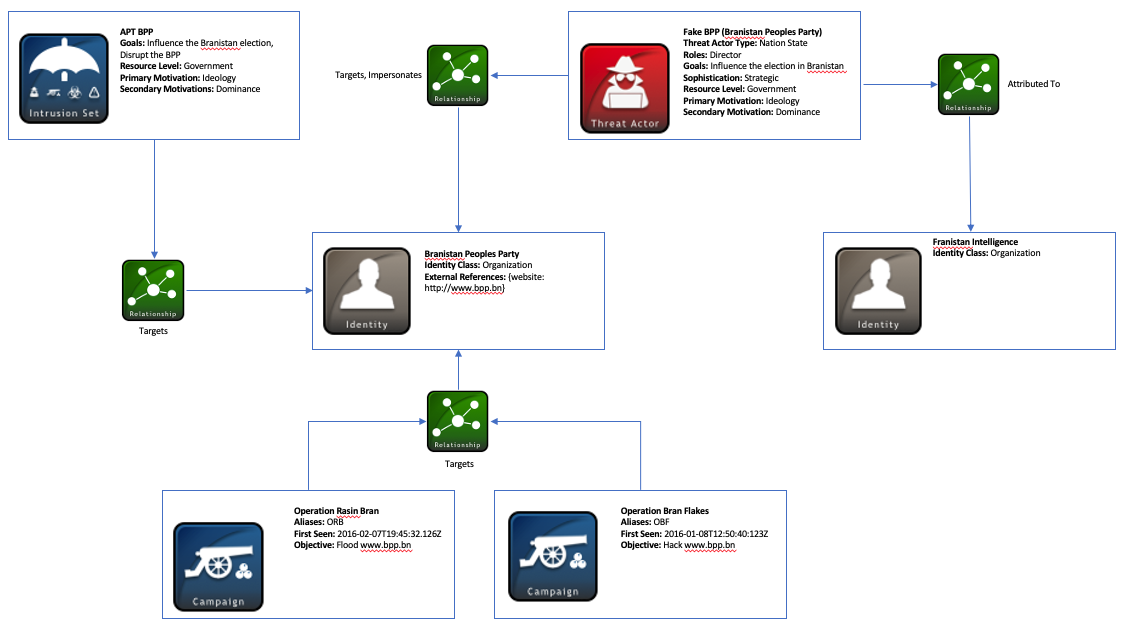
The next common relationship involves the Identity SDO of the Branistan People’s Party. In this case, the campaigns, intrusion set, and threat actor all target this identity, so the target_ref field would contain the identity ID of the BPP with the relationship_type being targets. In addition to these relationships, the threat actor, Fake BPP, is involved in other relationships between the Identity objects. Since Fake BPP is linked to the nation of Franistan, this Threat Actor SDO is related to the Franistan Identity SDO with a relationship_type of attributed-to. Also, in one of the attacks mentioned earlier, Fake BPP attempted to take over the real BPP’s website and post content posing as the real BPP, so another relationship is needed indicating that Fake BPP impersonates the real BPP.
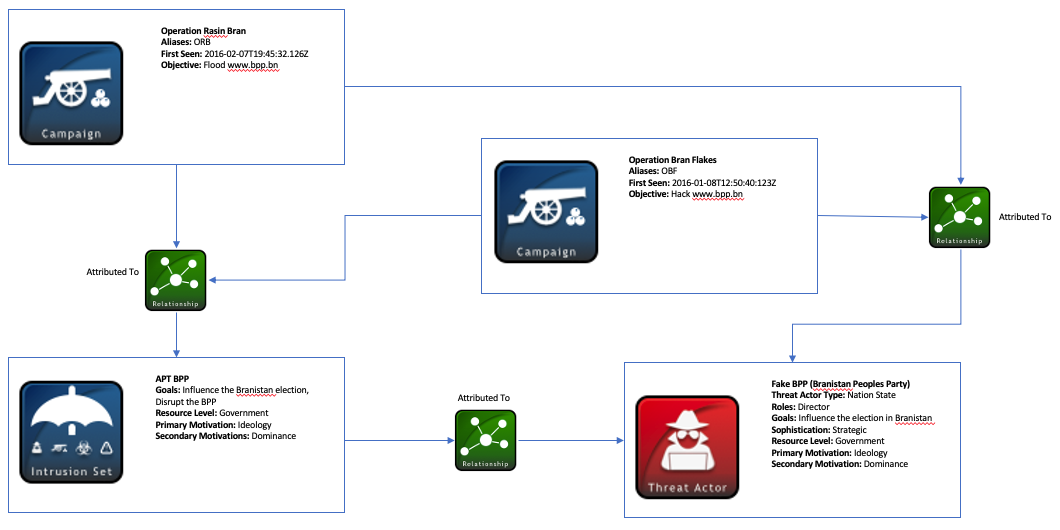
Finally, there are several more relationships that link the campaigns, intrusion set, and threat actor together. Both campaigns are attributed-to the Intrusion Set and Threat Actor SDOs (in separate relationships). Also, due to Intrusion Set representing the entire attack package orchestrated by this Threat Actor, the Intrusion Set SDO is attributed-to the Threat Actor object as well.
The following diagrams help visualize the relationships between the SDOs in this scenario. An interactive version can be found here. The first diagram below serves to represent the connections among the Intrusion Set, Threat Actor, and Campaign objects:
The second diagram below models the relationships among the Identity objects and Intrusion Set, Threat Actor, and Campaign SDOs:
Finally, the third diagram captures relationships between the Attack Pattern SDOs and the Intrusion Set, Threat Actor, and Campaign objects:
Further Reading
To read more about the objects in this example as well as common properties and vocabularies, check out the links below:
- Common Properties
- Vocabularies
- Intrusion Set
- Campaign
- Threat Actor
- Identity
- Attack Pattern
- Relationship
Implementation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
{
"type": "bundle",
"id": "bundle--97b40f76-c1b8-4407-b050-ff177f3d67ed",
"objects": [
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "Fake BPP (Branistan Peoples Party)",
"threat_actor_types": [
"nation-state"
],
"roles": [
"director"
],
"goals": [
"Influence the election in Branistan"
],
"sophistication": "strategic",
"resource_level": "government",
"primary_motivation": "ideology",
"secondary_motivations": [
"dominance"
]
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--8c6af861-7b20-41ef-9b59-6344fd872a8f",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "Franistan Intelligence",
"identity_class": "organization"
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "Branistan Peoples Party",
"identity_class": "organization",
"external_references": [
{
"source_name": "website",
"url": "http://www.bpp.bn"
}
]
},
{
"type": "attack-pattern",
"spec_version": "2.1",
"id": "attack-pattern--19da6e1c-71ab-4c2f-886d-d620d09d3b5a",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2017-01-30T21:15:04.127Z",
"name": "Content Spoofing",
"external_references": [
{
"source_name": "capec",
"url": "https://capec.mitre.org/data/definitions/148.html",
"external_id": "CAPEC-148"
}
]
},
{
"type": "attack-pattern",
"spec_version": "2.1",
"id": "attack-pattern--f6050ea6-a9a3-4524-93ed-c27858d6cb3c",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2017-01-30T21:15:04.127Z",
"name": "HTTP Flood",
"external_references": [
{
"source_name": "capec",
"url": "https://capec.mitre.org/data/definitions/488.html",
"external_id": "CAPEC-488"
}
]
},
{
"type": "campaign",
"spec_version": "2.1",
"id": "campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "Operation Bran Flakes",
"description": "A concerted effort to insert false information into the BPP's web pages.",
"aliases": [
"OBF"
],
"first_seen": "2016-01-08T12:50:40.123Z",
"objective": "Hack www.bpp.bn"
},
{
"type": "campaign",
"spec_version": "2.1",
"id": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "Operation Raisin Bran",
"description": "A DDOS campaign to flood BPP web servers.",
"aliases": [
"ORB"
],
"first_seen": "2016-02-07T19:45:32.126Z",
"objective": "Flood www.bpp.bn"
},
{
"type": "intrusion-set",
"spec_version": "2.1",
"id": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
"created": "2016-08-08T15:50:10.983Z",
"modified": "2016-08-08T15:50:10.983Z",
"name": "APT BPP",
"description": "An advanced persistent threat that seeks to disrupt Branistan's election with multiple attacks.",
"aliases": [
"Bran-teaser"
],
"first_seen": "2016-01-08T12:50:40.123Z",
"goals": [
"Influence the Branistan election",
"Disrupt the BPP"
],
"resource_level": "government",
"primary_motivation": "ideology",
"secondary_motivations": [
"dominance"
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--98765000-efdf-4a86-8681-36481ceae57f",
"created": "2020-02-29T17:41:44.938Z",
"modified": "2020-02-29T17:41:44.938Z",
"relationship_type": "attributed-to",
"source_ref": "campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
"target_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--53a55c73-f2c8-47b9-8e50-ae34d8c5da4d",
"created": "2020-02-29T17:41:44.938Z",
"modified": "2020-02-29T17:41:44.938Z",
"relationship_type": "attributed-to",
"source_ref": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"target_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--5047c2c0-524b-4afd-9cd6-e197efe59495",
"created": "2020-02-29T17:41:44.939Z",
"modified": "2020-02-29T17:41:44.939Z",
"relationship_type": "attributed-to",
"source_ref": "campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
"target_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--9cc131ca-b64d-4ab1-a300-5e4a0073280a",
"created": "2020-02-29T17:41:44.939Z",
"modified": "2020-02-29T17:41:44.939Z",
"relationship_type": "attributed-to",
"source_ref": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"target_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--c171fd27-2a8a-42b7-8293-34016b70c1c8",
"created": "2020-02-29T17:41:44.939Z",
"modified": "2020-02-29T17:41:44.939Z",
"relationship_type": "attributed-to",
"source_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
"target_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--554e3341-d7b1-4b3c-a522-28ef52fbb49b",
"created": "2020-02-29T17:41:44.939Z",
"modified": "2020-02-29T17:41:44.939Z",
"relationship_type": "targets",
"source_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--06964095-5750-41fe-a9af-6c6a9d995489",
"created": "2020-02-29T17:41:44.940Z",
"modified": "2020-02-29T17:41:44.940Z",
"relationship_type": "uses",
"source_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
"target_ref": "attack-pattern--19da6e1c-71ab-4c2f-886d-d620d09d3b5a"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4fe5dab1-fd6d-41aa-b8b1-d3118a708284",
"created": "2020-02-29T17:41:44.940Z",
"modified": "2020-02-29T17:41:44.940Z",
"relationship_type": "uses",
"source_ref": "intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
"target_ref": "attack-pattern--f6050ea6-a9a3-4524-93ed-c27858d6cb3c"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d8b7932d-0ecb-4891-b021-c78ff2b63747",
"created": "2020-02-29T17:41:44.940Z",
"modified": "2020-02-29T17:41:44.940Z",
"relationship_type": "targets",
"source_ref": "campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--96cfbc6f-5c08-4372-b811-b90fbb2ec180",
"created": "2020-02-29T17:41:44.940Z",
"modified": "2020-02-29T17:41:44.940Z",
"relationship_type": "targets",
"source_ref": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--33c22977-d104-45d8-be19-273f7ab03de1",
"created": "2020-02-29T17:41:44.940Z",
"modified": "2020-02-29T17:41:44.940Z",
"relationship_type": "uses",
"source_ref": "campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
"target_ref": "attack-pattern--19da6e1c-71ab-4c2f-886d-d620d09d3b5a"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--8848cba9-4c7b-4695-bc09-5033a6f20ff4",
"created": "2020-02-29T17:41:44.941Z",
"modified": "2020-02-29T17:41:44.941Z",
"relationship_type": "uses",
"source_ref": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"target_ref": "attack-pattern--f6050ea6-a9a3-4524-93ed-c27858d6cb3c"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--a97b3ea5-4ca1-46a0-a7ad-f10143ce22b2",
"created": "2020-02-29T17:41:44.941Z",
"modified": "2020-02-29T17:41:44.941Z",
"relationship_type": "impersonates",
"source_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4292a6df-fb16-43d1-805d-dc1b33946fdf",
"created": "2020-02-29T17:41:44.941Z",
"modified": "2020-02-29T17:41:44.941Z",
"relationship_type": "targets",
"source_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--4bd67b9e-d112-4ea6-98bb-080a051667c7",
"created": "2020-02-29T17:41:44.941Z",
"modified": "2020-02-29T17:41:44.941Z",
"relationship_type": "attributed-to",
"source_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"target_ref": "identity--8c6af861-7b20-41ef-9b59-6344fd872a8f"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--1f4ee02a-7f6e-45a6-aedd-c1492af5e179",
"created": "2020-02-29T17:41:44.942Z",
"modified": "2020-02-29T17:41:44.942Z",
"relationship_type": "targets",
"source_ref": "campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
"target_ref": "identity--ddfe7140-2ba4-48e4-b19a-df069432103b"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--ba30893a-400a-43f3-b193-69d65d2a8f40",
"created": "2020-02-29T17:41:44.942Z",
"modified": "2020-02-29T17:41:44.942Z",
"relationship_type": "uses",
"source_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"target_ref": "attack-pattern--19da6e1c-71ab-4c2f-886d-d620d09d3b5a"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--70880ead-0b19-4785-be52-a69064d4cb6c",
"created": "2020-02-29T17:41:44.942Z",
"modified": "2020-02-29T17:41:44.942Z",
"relationship_type": "uses",
"source_ref": "threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
"target_ref": "attack-pattern--f6050ea6-a9a3-4524-93ed-c27858d6cb3c"
}
]
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
from stix2.v21 import (ThreatActor, Identity, AttackPattern, Campaign, IntrusionSet, Relationship, ExternalReference, Bundle)
threat_actor = ThreatActor(
type="threat-actor",
spec_version="2.1",
id="threat-actor--56f3f0db-b5d5-431c-ae56-c18f02caf500",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="Fake BPP (Branistan Peoples Party)",
threat_actor_types=["nation-state"],
roles=["director"],
goals=["Influence the election in Branistan"],
resource_level="government",
primary_motivation="ideology",
secondary_motivations=["dominance"],
sophistication="strategic"
)
identity1 = Identity(
type="identity",
spec_version="2.1",
id="identity--8c6af861-7b20-41ef-9b59-6344fd872a8f",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="Franistan Intelligence",
identity_class="organization"
)
ref_bpp = ExternalReference(
source_name="website",
url="http://www.bpp.bn"
)
identity2 = Identity(
type="identity",
spec_version="2.1",
id="identity--ddfe7140-2ba4-48e4-b19a-df069432103b",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="Branistan Peoples Party",
identity_class="organization",
external_references= [ref_bpp]
)
ref_capec1 = ExternalReference(
source_name="capec",
url="https://capec.mitre.org/data/definitions/148.html",
external_id="CAPEC-148"
)
ref_capec2 = ExternalReference(
source_name="capec",
url="https://capec.mitre.org/data/definitions/488.html",
external_id="CAPEC-488"
)
attack_pattern1 = AttackPattern(
type="attack-pattern",
spec_version="2.1",
id="attack-pattern--19da6e1c-71ab-4c2f-886d-d620d09d3b5a",
created="2016-08-08T15:50:10.983Z",
modified="2017-01-30T21:15:04.127Z",
name="Content Spoofing",
external_references=[ref_capec1]
)
attack_pattern2 = AttackPattern(
type="attack-pattern",
spec_version="2.1",
id="attack-pattern--f6050ea6-a9a3-4524-93ed-c27858d6cb3c",
created="2016-08-08T15:50:10.983Z",
modified="2017-01-30T21:15:04.127Z",
name="HTTP Flood",
external_references=[ref_capec2]
)
campaign1 = Campaign(
type="campaign",
spec_version="2.1",
id="campaign--e5268b6e-4931-42f1-b379-87f48eb41b1e",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="Operation Bran Flakes",
description="A concerted effort to insert false information into the BPP's web pages.",
aliases=["OBF"],
first_seen="2016-01-08T12:50:40.123Z",
objective="Hack www.bpp.bn"
)
campaign2 = Campaign(
type="campaign",
spec_version="2.1",
id="campaign--1d8897a7-fdc2-4e59-afc9-becbe04df727",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="Operation Raisin Bran",
description="A DDOS campaign to flood BPP web servers.",
aliases=["ORB"],
first_seen="2016-02-07T19:45:32.126Z",
objective="Flood www.bpp.bn"
)
intrusionset = IntrusionSet(
type="intrusion-set",
spec_version="2.1",
id="intrusion-set--ed69450a-f067-4b51-9ba2-c4616b9a6713",
created="2016-08-08T15:50:10.983Z",
modified="2016-08-08T15:50:10.983Z",
name="APT BPP",
description="An advanced persistent threat that seeks to disrupt Branistan's election with multiple attacks.",
first_seen="2016-01-08T12:50:40.123Z",
resource_level="government",
primary_motivation="ideology",
goals=["Influence the Branistan election", "Disrupt the BPP"],
secondary_motivations=["dominance"],
aliases=["Bran-teaser"]
)
relationship1 = Relationship(campaign1, 'attributed-to', threat_actor)
relationship2 = Relationship(campaign2, 'attributed-to', threat_actor)
relationship3 = Relationship(campaign1, 'attributed-to', intrusionset)
relationship4 = Relationship(campaign2, 'attributed-to', intrusionset)
relationship5 = Relationship(intrusionset, 'attributed-to', threat_actor)
relationship6 = Relationship(intrusionset, 'targets', identity2)
relationship7 = Relationship(intrusionset, 'uses', attack_pattern1)
relationship8 = Relationship(intrusionset, 'uses', attack_pattern2)
relationship9 = Relationship(campaign1, 'targets', identity2)
relationship10 = Relationship(campaign2, 'targets', identity2)
relationship11 = Relationship(campaign1, 'uses', attack_pattern1)
relationship12 = Relationship(campaign2, 'uses', attack_pattern2)
relationship13 = Relationship(threat_actor, 'impersonates', identity2)
relationship14 = Relationship(threat_actor, 'targets', identity2)
relationship15 = Relationship(threat_actor, 'attributed-to', identity1)
relationship16 = Relationship(campaign2, 'targets', identity2)
relationship17 = Relationship(threat_actor, 'uses', attack_pattern1)
relationship18 = Relationship(threat_actor, 'uses', attack_pattern2)
bundle = Bundle(objects=[threat_actor, identity1, identity2, attack_pattern1, attack_pattern2, campaign1, campaign2, intrusionset, relationship1, relationship2, relationship3, relationship4, relationship5, relationship6, relationship7, relationship8, relationship9, relationship10, relationship11, relationship12, relationship13, relationship14, relationship15, relationship16, relationship17, relationship18])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
import stix2
import re
for obj in bundle.objects:
if obj == threat_actor:
print("------------------")
print("== THREAT ACTOR ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Threat Actor Types: " + str(obj.threat_actor_types))
print("Roles: " + str(obj.roles))
print("Goals: " + str(obj.goals))
print("Sophistication: " + obj.sophistication)
print("Resource Level: " + obj.resource_level)
print("Primary Motivation: " + obj.primary_motivation)
print("Secondary Motivations: " + str(obj.secondary_motivations))
elif obj == identity1:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Identity Class: " + obj.identity_class)
elif obj == identity2:
print("------------------")
print("== IDENTITY ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Identity Class: " + obj.identity_class)
elif obj == attack_pattern1:
print("------------------")
print("== ATTACK PATTERN ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Type: " + obj.type)
print("External References: " + str(obj.external_references))
elif obj == attack_pattern2:
print("------------------")
print("== ATTACK PATTERN ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Type: " + obj.type)
print("External References: " + str(obj.external_references))
elif obj == campaign1:
print("------------------")
print("== CAMPAIGN ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Aliases: " + str(obj.aliases))
print("First Seen: " + str(obj.first_seen))
print("Objective: " + obj.objective)
elif obj == campaign2:
print("------------------")
print("== CAMPAIGN ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.description)
print("Type: " + obj.type)
print("Aliases: " + str(obj.aliases))
print("First Seen: " + str(obj.first_seen))
print("Objective: " + obj.objective)
elif obj == intrusionset:
print("------------------")
print("== INTRUSION SET ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Name: " + obj.name)
print("Description: " + obj.name)
print("Type: " + obj.type)
print("Aliases: " + str(obj.aliases))
print("First Seen: " + str(obj.first_seen))
print("Goals: " + str(obj.goals))
print("Resource Level: " + obj.resource_level)
print("Primary Motivation: " + obj.primary_motivation)
print("Secondary Motivations: " + str(obj.secondary_motivations))
elif re.search('relationship*', str(obj)):
print("------------------")
print("== RELATIONSHIP ==")
print("------------------")
print("ID: " + obj.id)
print("Created: " + str(obj.created))
print("Modified: " + str(obj.modified))
print("Type: " + obj.type)
print("Relationship Type: " + obj.relationship_type)
print("Source Ref: " + obj.source_ref)
print("Target Ref: " + obj.target_ref)